Robert Lychev, Georgia Tech, Sharon Goldberg, Boston University
Transcription
Robert Lychev, Georgia Tech, Sharon Goldberg, Boston University
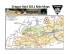
ARE WE THERE YET? QUANTIFYING BGP SECURITY IN PARTIAL DEPLOYMENT Robert Lychev Sharon Goldberg Michael Schapira Boston University Hebrew University Georgia Tech Abstract The Border Gateway Protocol (BGP) sets up routes between the smaller networks that make up the Internet. In the protocol, each autonomous system (AS) --- an independent network administrated by a single profitseeking entity --- maintains a list of possible routes to various VZW: ISP 1: Level3, VZW, 22394 66.174.161.0/24 (Level3, VZW, 22394, Prefix) ISP 1 after securing just one more node AS 31283, AS 2905 switches to a route through attacker AS 3340 reachability information traffic flow Level 3 Verizon Wireless China Telecom VZW: (22394, Prefix) 22394 Level3: (VZW, 22394, Prefix) VZW: malicious router cannot announce a direct route to 22394, since 22394 never said (22394, Prefix) ChinaTel: (22394, Prefix) The Internet has about 40K ASes with competing interests, so not all of them can be secured at the same time! before AS 31283 deploys S-BGP after AS 31283 deploys S-BGP and when security is second or third … Who must be secured first? What are our objectives and obstacles? Background and Motivation reachability information traffic flow (22394, Prefix) Level3: (VZW, 22394, Prefix) destinations. Such reachability information is disseminated globally as each AS selects its most preferred routes to the corresponding destinations and advertises them to its neighboring ASes. Despite its crucial role, BGP is notoriously vulnerable to serious problems, including propagation of bogus routing information due to attacks or misconfigurations and network instabilities in the form of persistent routing oscillations. The S*BGP protocols (Secure BGP, secure origin BGP, BGPsec, etc) were proposed to address these issues. However, even if S*BGP protocols were to ever reach complete Internet-wide deployment, they are bound to go through a phase of incremental deployment, where ASes decide if and when to deploy such protocols. In this initial phase, secure and non-secure versions of BGP will have to coexist. This coexistence of BGP and S*BGP gives rise to many unanswered questions about BGP security under partial deployment (i.e. when some ASes have deployed S*BGP, but others have not). By combining theoretical analyses with multiple large-scale simulations on empirical data, we address many important questions such as ``What security guarantees are achievable under partial deployment and how to quantify them?'', ``What new vulnerabilities are introduced into the interdomain routing system?'', ``Under what conditions is S*BGP guaranteed to converge even in presence of attackers?'', ``Which ASes are the most important to secure?'', and many more. By word of mouth smaller networks such as ATT, BU, Verizon, etc., use BGP to set up routes to various destination IP prefixes. This is what glues the Internet together! As security is given higher priority, it affects more ASes, but when security is second or first … with a blackhole attack, AS 4559 attracts AS 111 that used a secure route before the attack HPC Provider in Texas Our objective is to minimize the amount of traffic that an attacker attracts with its attack. peers exchange traffic for free Theorem: The problem of minimizing the number of ASes that a particular attacker attracts with its attack is NP-hard . *Remark: In reality, our job is harder because we do not know where the attacker is. ISP 1 Boston University Inconsistent prioritization of security across secure ASes can lead to BGP Wedgies Level 3 Verizon Wireless China Telecom Telecom provider in southeast Asia and unpredictable network behavior VZW, 22394 66.174.161.0/24 Level3, VZW, 22394 66.174.161.0/24 that is difficult to debug. 22394 before the blackhole attack after the blackhole attack 22394 66.174.161.0/24 When selecting a favorite route, every node must consider: local preferences (business relationship with its neighbor on that route) and route length. Priority for security can be considered before local preferences (first), after route length (third), and in between (second). Unfortunately, to attract/intercept traffic, a malicious AS can pretend to connect to a valid origin directly. A similar incident happened in April 2010 involving China Telecom and some US government sites. Swedish ISP places security below local preferences $ customer routes are preferred to provider routes Level3, VZW, 22394 66.174.161.0/24 Theorem: security non-monotonicity and protocol downgrades do not occur when security is 3rd and 1st respectively, for networks that satisfy well-known properties such as GR conditions [1]. customer pays its provider reachability information traffic flow ChinaTel, 22394 66.174.161.0/24 peer routes are preferred to provider routes Empirically, non-monotonicity and protocol downgrades do not seem to pose a major issue in general. This suggests that higher prioritization of security may result in more benefit to the Internet overall. Norwegian ISP prioritizes security above everything Level 3 China Telecom Verizon Wireless 22394 Average Fraction of Sources ISP 1 Sec 1st Sec 2nd Sec 3rd Sec 1st Sec 2nd Sec 1st Sec 2nd Sec 3rd does not deploy S-BGP Using Public Key Cryptography, S-BGP prevents ASes from announcing prefixes they do not own as well as routes that were not announced to them. This requires Public Key Cryptography (PKI). When top 12 tier-2 ASes and their biggest Stubs are secured, ~3000 ASes in total. Theorem: when all secure ASes prioritize security the same way, S-BGP converges to a unique stable state, for networks that satisfy well-known properties such as GR conditions [1]. References: [1] L. Gao and J. Rexford. Stable Internet routing without global coordination. Trans. On Networking, 2001. [2] On Blind Mice and the Elephant, An Aqua Lab Project, www.aqualab.cs.northwestern.edu/projects/BlindMice.html.
Similar documents
Border Gateway Protocol
 Provider1 won’t peer with Provider2 in Singapore; Provider2 must
drag traffic to San Jose to hand it off to Provider1, who drags it
home again to Singapore.
Provider1 won’t peer with Provider2 in Singapore; Provider2 must
drag traffic to San Jose to hand it off to Provider1, who drags it
home again to Singapore.